Table of Contents
Introduction
Just recently, REvil, one of the most notorious hacking groups that came as mysteriously as they recently went, launched a series of attacks on hundreds of companies across the globe. The attack group went ahead to demand millions from its victims. The most recent REvil attack was on Kaseya VSA, a software provider. It spread malware to hundreds of Kaseya subscribers. It also forced JBS, one of the largest meat processors, to pay a ransom fee of $11 Million before gaining control of its systems.
https://threatpost.com/revil-ransomware-code-rivals/167167/
Indeed, the REvil ransomware has been one of the most notorious hacking groups that have come up in the recent past. This article will explore REvil ransomware, learn what it is, why it is a unique hacking group, how it works, and some security measures that you can put in place to protect yourself from REvil attackers.
What is REvil?
The REvil came to light in April 2019 following the extinction of another notorious hacking group referred to as gang GandCrab.
REvil, which is sometimes referred to as Sodin or Sodinokibi, has gained a reputation for its behavior of wanting to extort an unusually large amount of payments from its corporate victims more than other attacks would do. As it has occurred, the REvil group is an actively promoted underground hacking forum that is dubbed as “the best choice” for attacking business networks that have more money to dish out than home users.
Although REvil’s primary focus is big organizations and businesses, this is no reason for individuals to sit back and relax. You never know when the hackers will come after you.
How REvil Ransomware works
Before we proceed to other details about REvil, it would be essential to understand what REVil ransomware is and how it works.
A REvil ransomware refers to a file-blocking malware-type attack that works by encrypting sensitive company files and discarding a request message for a ransom payment. According to the message, the ransom payment should be made in Bitcoin. The message also warns the victims that failure to pay the ransom on time will double the ransom fee.
Upon payment of the Ransom fee, the victim is given back all his files and full access to their system.
What makes REvil so unique?
Ransomware attacks have always been here with us since time immemorial. According to Datto’s Global State of Channel Ransomware Attack Report, 1 out of every 5 SMBs has reported falling victims to a Ransomware attack. This is to say that REvil ransomware is just one of the many ransomware attacks that have occurred before.
However, the question that we should all seek to answer today is why REvil is the most unique of all ransomware attacks.
The popularity of REvil has mainly been affected by its attempt to extort large amounts of ransom fees from its victims. REvil ransomware is also known to attack large corporations, unlike other ransomware attacks.
REvil was Ransomware-as-a-service. What’s that?
You will probably hear or read about REvil being a Ransomware-as-a-service. What does it mean by Ransomware-as-a-service?
Ransomware-as-a-service (RaaS) is a businesswise model that ransomware developers mainly use to lease out already-developed ransomware variants to interested subscribers who wish to carry out ransomware attacks but do not have the expertise and adequate skills to do so.
As such, Ransomware-as-a-service gives people, even those without the technical know-how, the ability to launch a ransomware attack. All one has to do is subscribe to Ransomware-as-a-service service. Usually, the RaaS kits are available on the dark web for purchase by interested buyers. They are advertised just like other products are advertised on our typical markets.
RaaS kits come at different prices. They usually range from 40 dollars per month to Millions of dollars, depending on their efficiency in executing a malware attack. As it has occurred, ransomware kits are in high demand. In general, there is a growing demand for ransomware attacks. In the third quarter of 2020, the demand rose to $234,000, and the trend is showing no signs of stopping.
REvil ransomware is classified as ransomware-as-a-service, sold out by a hacking group referred to as PINCHY SPIDER. Pinchy Spider sells ransomware-as-a-service under the affiliate model and takes 40% of all the profits accrued in ransomware payments.
How much money is the REvil enterprise making?
It is hard to ascertain the amount of money that the REvil hacking group is making. However, according to the group developers, REvil hacking group makes over $100 million per annum through targeting large enterprises to extort money from them. REvil targets large corporations across all sectors.
According to the group developers, the REvil hacking group is now looking to increase its profits to $2 billion by adopting more sophisticated ransomware techniques and trends in its undying pursuit of wealth.
As already mentioned, REvil operates a ransomware-as-a-service business model, in which they sell out ransomware services to interested subscribers. Apart from the heavy subscription fees involved in leasing such tools, the REvil group also keeps a huge chunk of the profits earned in the form of the ransom fee paid.
It means that the REvil hacking group is the one that sets up the ransom fee, runs through all the negotiations, and collects the ransom fee that is later distributed to its affiliates. From their operations, we can easily deduce that the REvil hacking group is a multi-billion dollar group.
How successful is REvil?
Apart from looking at how much the REvil group makes from its malicious undertakings, we can also check how successful the REvil group is by looking at its victims and the extent of the impact they caused to the victims.
One of the key successes of the REvil attack is the recent Kaseya VSA attack. Kaseya is an IT solution developer for enterprise clients. The attack took place on the third day of July 2021, at around 10:00 AM EST. Upon carrying out the ransomware attack, the REvil group posted a message, as shown in the attached image.
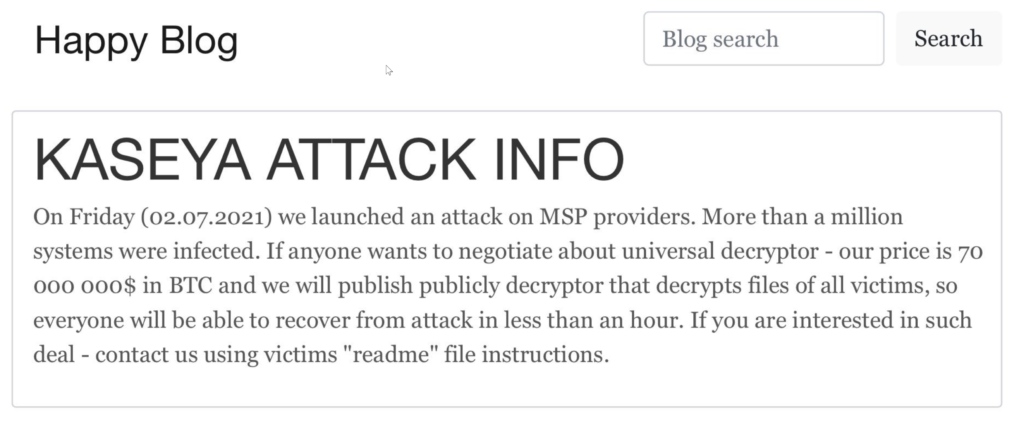
As it seems, Kaseya VSA was vulnerable to an SQL injection which the REvil attackers leveraged to carry out one of their most successful attacks.
Apart from the Kaseya VSA attack, the REvil group is also known for a series of ransomware attacks that targeted companies such as the following;
- GEDIA Automotive Group
- Albany International Airport
- Brown-Forman
- Grubman Shire Meiselas & Sacks law firm
- SeaChange International
- Artech Information Systems
In one way or another, all the names mentioned above have faced the wrath of the REvil ransomware.
How does the REvil ransomware infect an organization
The next element regarding the REvil ransomware is to understand how the ransomware is spread.
There are several techniques that the REvil ransomware group can use to plant malware and spread infection through a system. Mostly, the REvil exploits the existing vulnerabilities in a system to gain unauthorized access to a computer on your company’s network. Moreover, the REvil also exploits social engineering attacks such as phishing and spear-phishing schemes. They will lure your employees into downloading a malicious link that will be executed to let them inside your network, steal data, and compromise your entire network.
In some rare cases, the attackers could use your clients or business prospects who have already fallen victim to the hackers.
How to Prevent REvil Ransomware
You could do a few things to prevent your system from ransomware attacks, such as the evil REvil. The following are some of the measures that you could take to ensure that you are safe.
- Conduct regular patches on your computers and systems. One of the critical elements you should regularly patch is the Bluekeep vulnerability link to the RDP attacks.
- Never click on an unsafe link or attachments from unknown sources or websites. Clicking on malicious links could automatically start a download that could lead to your entire system being compromised or opening up doors for ransomware attackers such as the REvil ransomware group.
- Do not disclose your sensitive or personal information to anyone. Usually, cybercriminals tend to collect personally sensitive data and information before an attack. For instance, whenever you receive a call, email, or text message looking to solicit sensitive data from you, it would be wise to withhold any material information that could lead you directly into the arms of ransomware attackers such as the REvil group. As a best practice, never give out sensitive data and information such as login credentials and passwords.
- Never use insecure or unknown USB drives for your company operations. Connecting a USB stick whose source is in question could render your storage sources vulnerable to attacks. Cybercriminals might have infected the USB drive and will execute an attack on your system the moment you insert the USB stick in your storage source.
- Always ensure that you frequently carry out upgrades to your software and operating systems. System and software updates usually come with enhanced security features that could help eradicate the loopholes that could make you vulnerable to cyber-attacks such as ransomware. And you never know who the attacker could be. It could just be the evil REvil gang that will leave your entire organization in shambles.
- Use only known sources to download files. Doing so will help to minimize the risks of downloading a ransomware attachment that could compromise your entire system. Additionally, it would be best if you only relied on verified vendors to get your software and applications. You can check out their trust seals to establish whether or not they are authentic. Browse sites that have an SSL certificate installed. Look out for the grey padlock and the HTTPS in the site url. This will ensure the confidentiality of the PII that you share with such a site.
- Use tools such as virus scanners and content filters that will scan through your entire system to discover and wipe out ransomware infections.
- Always use a virtual private network when using public Wi-Fi.
What To Do if You Fall Victim to REvil Attack group
The hardest decision you would have to make if you fall victim to a REvil ransomware attack or any other kind of ransomware attack is whether or not to pay the ransom. The more the organizations pay ransom to the REvil group, the more the criminals get motivated to launch similar attacks in the future.
However, you will be at crossroads because your businesses might not survive without the withheld systems and data. So you are compelled to pay the ransom.
Whatever the decision you decide to work with, it is vital that you speedily inform the law enforcement agencies about the occurrence of the ransomware and help them investigate who might be the criminals behind the attack.
Lastly, you must remember that paying the ransom fee does not guarantee that you will receive back your data or erase the security threats that might come by. Therefore, you must evaluate your entire cybersecurity strategy to discover what went wrong and rectify it to avoid future challenges.
Conclusion
The REvil group has caused a lot of harm to multiple victims. Although the group recently disappeared from the public view, it is vital to understand how the REvil malware operated to secure your system from such an attack and many more that might come by. This article has given you some insights into how the REvil malware worked and some of the things you should do to protect yourself from such attacks.




